Dropped USB flash drives are still effective means for getting into networks. The goal of this post is to give you a bit of a hands on lab and show you some tricks for actually conducting USB drop attacks, including how to prepare the payload using Core Impact.
USB drop attacks are a bit of a performance art form. You need to build an enticing story that’ll make the discoverers of the drop, whom I will refer to as ‘The Marks’, curious enough to override common sense and plug in the stick to figure out what’s on it.
First off, you need to be very selective about where you leave these things. You need to put them in places where it is almost certain that the folks who pick them up will plug them in inside the target network, not elsewhere. Office lobbies, parking lots, and break rooms are some of my personal favorites. Make sure that you explicitly include this type of attack as permissible in your Rules of Engagement for the test you’re conducting.
Secondly, when you’re picking a device to use, you can get bulk packs from your favorite retailer. I find 10 packs of 2GB sticks for about $20-$25 all over the place. Stick with cheap units, because you’ll never see most of these again. You’ll also want to get a variety of colors and form factors. There’s a couple of things that you can do that’ll enhance the look of the devices. Brand spanking new flash drives are more than a little bit suspicious. You’ll want to dirty them up a bit, or distress them, in special effects industry parlance. My favorite quick trick for distressing flash drives involves tossing a couple of drives into a cloth bag, with a spoonful of sand, and a handful of dryer lint. Put the whole bag into a dryer for 15 minutes on the tumble, or no heat setting.
Attaching the flash drive to a key ring then hanging keys from it helps, so long as the keys aren’t new and shiny as well. Ebay is a perfect resource for finding collections of keys, both for standard locks, and for vehicles. I’ve also had great luck with attaching a proximity badge to the flash drive and putting them both on a retractable badge holder. For added verisimilitude, attach a frequent shopper club barcode to it, too.
From my experience, the marks are most likely to plug in a flash drive that looks like it’s part of something important to someone. The car keys work the very best. To create a USB drop attack using Core Impact, there’s two different techniques we can use. The first involves creating an executable agent with an auto-run.
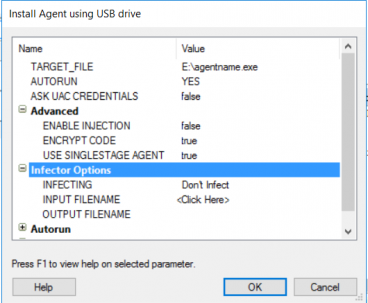
- Open a new Impact Workspace, and switch to the module tab.
- Search for “Install Agent using USB drive”
- Double-click on the Module
- Set the target file for the location of the flash drive.
For advanced usage, you can use an infected Excel spreadsheet or Adobe Acrobat PDF file from this same module. Make sure that you take a look at the connection options for non-permissive environments. HTTPS tends to be the most reliable in most environments, but your mileage will vary.
Good luck, and happy hacking!
Safeguard Your Infrastructure and Data
Access a collection of penetration testing resources and tools for keeping your cyber assets safe.