Core Impact 2017 R1 and Metasploit Pro are tools used to create multi-staged, real-world attacks to test enterprise security defenses. Organizations need improved visibility into the the holes in their enterprise network defenses. Pen Testing tools allow an organization to evaluate their ability to detect, prevent, and respond to attacks using multi-staged, real-world attacks.
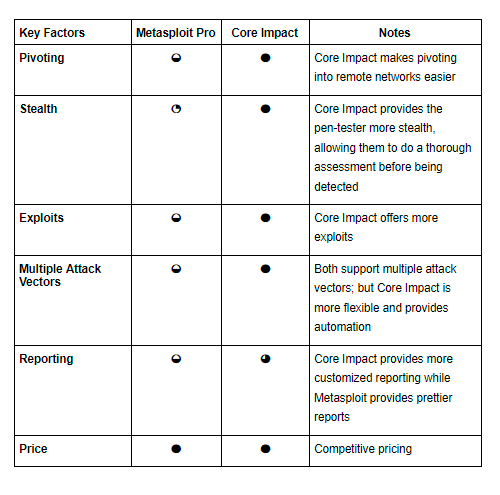
Both Core Impact and Metasploit Pro have a large following, but there are several areas in which they are different that dramatically increase a Pen-Tester’s ability to do their job:
Pivoting
Once a penetration tester (aka pen-tester) has established a foothold into a remote network (by compromising a machine that has access to both the internal and external network), he/she wants to behave like an attacker and Pivot, or move throughout the network by accessing other machines and compromising them by taking advantages of other vulnerabilities. Pivoting allows an attacker (or pen-tester in this case) to move throughout the network to find valuable data while obtaining credentials along the way. Easy right? Not exactly, but pen-testing tools make it possible.
With Core Impact, you get an easy and intuitive pivoting workflow. From any system you have established a foothold within, you can right-click and tell Impact to automatically pivot to neighboring devices and exploit them. You're done! With its lightweight design, you only need the proxy sys calls or API calls on the target; all else is handled by the console.
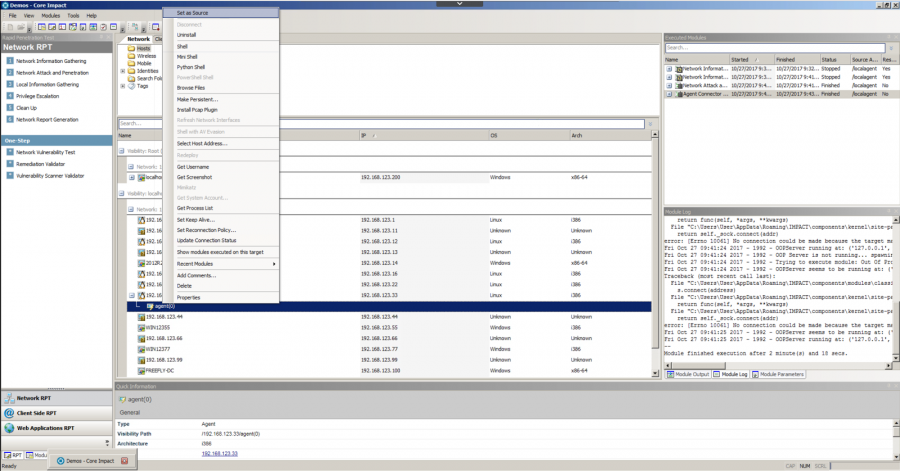
Core Impact also supports PCAP (packet capture) installation on pivoted systems, enabling stealthy information gathering of the device’s network traffic as well as faster port and service scanning capabilities.
With Metasploit Pro, you can pivot but you can only do so by proxies or through VPNs that the user has to configure. This is helpful, but requires significant overhead and effort that isn’t necessary and doesn’t emulate how a real attacker would most likely behave.
Stealth
For attackers, being stealthy is critical - they can’t afford to be found. Similarly, pen-testers want to avoid detection. Often this requires patience as it takes time to identify vulnerabilities within an organization without being detected and blocked.
To do this type of in-depth reconnaissance, the pen-tester will need time to learn as much as they can about your target network, including which services are being used along with devices and software. Once they know this information, they can compare it with a list of known vulnerabilities to come up with a list to potentially target for exploitation.
To remain hidden, Core Impact supports agentless shells and persistence through WMI (Windows Management Instrumentation). This allows for much stealthier interactions with systems and lets the user obtain persistence by allowing remote access to Windows OSs and applications in a way that is common in most companies.
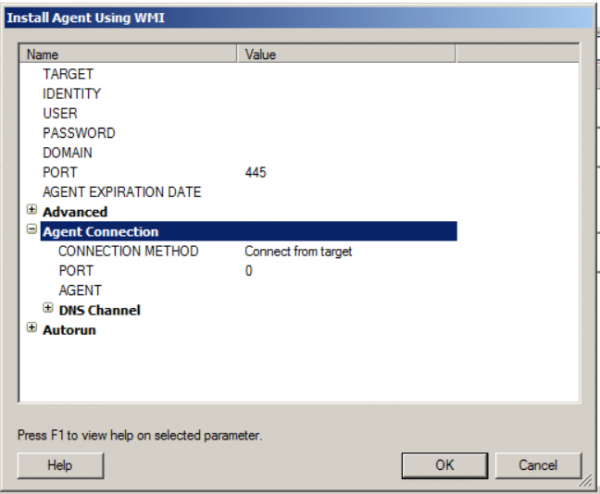
Depending upon your testing needs, stealth may or may not be necessary. But if it is, then you are better off to go with Core Impact as Metasploit does not support agentless shells or WMI persistence. For example, if conducting a test aimed at replicating the way a bad actor would attack a network, it is important to keep the noise made in the network to a minimum. Utilizing WMI shells and persistence is one way that Core Impact can help with this.
Number of Exploits
At the end of the day, a Pen-Tester’s ability to exploit a vulnerable system is paramount. Both Metasploit Pro and Core Impact include the latest exploits available. Metasploit Pro has an open framework where exploit writers around the world can contribute. Core takes a different approach by crafting their own commercial grade exploits by their CoreLabs team.
With Core Impact, you get more commercial grade exploits (1,836) than Metasploit Pro (1,429). Core Impact also supports all of the additional unique exploits from Metasploit Pro, bringing the total exploits for Core Impact to 2,163. This gives Core Impact over 700 more exploits than Metasploit Pro. Core Impact also offers an optional SCADA Exploits pack.
Multiple Attack Vectors
Today attackers don’t limit themselves to a single attack vector as they move through an organization’s network. They might use Phishing to infect an initial client-side device followed by taking advantage of network vulnerabilities to move throughout the network. A properly executed pen test should also include multiple attack vectors to be performed against the same network.
Metasploit supports multiple attack vectors but it is a manual process. While often attackers also utilize multiple attack vectors in a manual way; pen testers benefit from automation.
Core Impact allows the user to replicate multi-staged attacks that can pivot across devices and applications. For example, when a pen-tester infiltrates a network and accesses critical data they likely have used multiple attack vectors. After they report their findings, it is important to be able to come back later and validate the fixes have been properly implemented. Core Impact allows for you to automatically rerun the exact attack paths used initially that resulted in a full penetration, thus ensuring that the patch/remediation was successful. A simple one-click test allows for the user to check if patching and remediation efforts were successful.
Reporting
While both products can produce reports, it’s important to get the most value from the results:
- Customized for the reader: The world’s most beautiful reports are useless if they don’t translate the results of penetration tests into a language that the reader can understand. Your reports need to be customized to represent the reader’s business, priorities, and concerns.
- Concerns: When you provide reports, show the reader the risks and concerns that are specific to their business and offer advice on how to remediate the vulnerabilities.
- Verify the information: Verify all vulnerabilities that the pen-tester discovered to make sure there are no false positives.
- Provide proof: Give the reader evidence that you were able to compromise their system. Screenshots are a great way to do this.
Core Impact offers highly customizable reports with the ability to save custom templates for future use. This customization is easy and intuitive, similar to an Excel template, and allows for adding (and even removing) additional tables, graphs, and images to make sure the reports you are creating have all the appropriate information and that it is displayed in a way that’s appropriate for the target audience. Core Impact also enables reporting across all vectors from one product.
Metasploit provides exceptional executive level reports that could be presented at any board meeting; however, they struggle to provide the workflow and level of customization necessary for most pen-testing teams.
Summary
Metasploit Pro and Core Impact are both market leaders in the pen-testing tool space. While Metasploit has a bigger user base and more know how to use what was once an open-source tool, Core Impact has the better overall solution and is now priced to compete. Both are great solutions that empower pen-testers to mimic attacker behaviors and test a company's defenses. Whichever solution your organization chooses, the important thing is to test and test often to reduce your organization's attack surface.