Here’s the scenario: You’ve compromised a system but it hasn’t been logged into recently by an administrator, so you’re quite disappointed by your Mimikatz results. You’ve got local system credentials but nothing that’s on the domain except the machine account. Your mission: do something with the system that will attract the attention of someone with administrator credentials and make them log into the system WITHOUT setting off enough alarm bells to trigger a full blown incident response. You’re leaving delicious bait out to attract our quarry, in this case a system administrator.
How can we do this? What sets off alarm bells? Excessive CPU usage? Oh yes. Running low on disk space? Totally. Weird event-log entries? Occasionally, but that depends on how carefully the environment is monitored. We don’t want to actually run the risk of knocking a system over, so filling up the disk is right out. Generating suspicious event-logs are too iffy on detection and, if they are noticed, might seriously kick off a full blown incident response. So that leaves us with spiking a CPU core. Notice that I say a CPU core, not all the cores. We don’t want to launch a denial of service on the machine.
Core Impact doesn’t have any modules for this exact purpose but does give us a rather excellent set of tools for improvisation. Impact has a rich and complex framework where you, the end user, can exploit this power to build your own modules and exploits as well as access the internals of the product directly. All of our exploit, post-exploit and information gathering modules are built using Python. In fact, when you deploy an agent onto a target system, we bring our own python interpreter with us requiring no additional software to be installed on the target. This is more of a “Be Prepared” strategy, and it’s very useful. To launch a python shell from an agent all you have to do is right-click on the agent, then select “Python Shell”. It’s really complex.
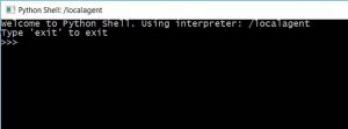
From here, you can import any available Python modules, build functions and generally do whatever you want to in a Pythonic fashion. A quick consulting trip to StackExchange leads us to a convenient page on how to spike a CPU with the smallest amount of code in a number of languages.
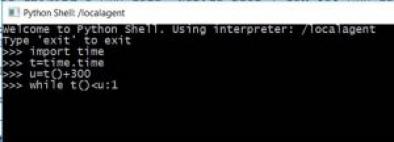
I’ve put 300 in here as the number of seconds to spike the CPU. Once you start executing it, close the shell. It’ll continue running full blast on the target system.
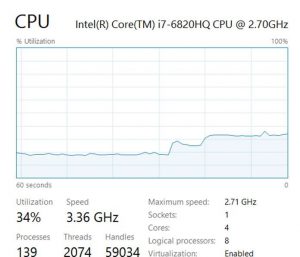
This should get their attention…then come back in an hour or so and rerun Mimikatz. You’ll probably catch an administrator credential. Either way, you will have helped to locate and, hopefully, to solve a dangerous behavior in your network and in your staff.