Chapter 2 | Verify Origins and Authenticity
In order to avoid alterations by unauthorized users or threat actors, system commands and files have built in cryptographic integrity protections. When system commands and files are added to a package, they’re embedded with a cryptographic hash. This acts as a virtual embossed seal and serves as validation that the file is the original version that came from the vendor—nothing has been added, copied, or altered. This provides confirmation that it is not a false version of the file, and that nothing malicious has been added, like a backdoor that attackers can use to exploit the system.
You can verify that the cryptographic hash matches vendor values by running the following command:
# rpm -Va | grep '^..5’
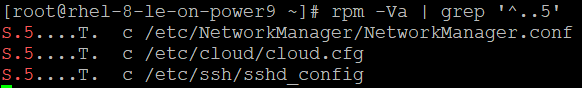
It is worth noting that not all alterations indicate that something is wrong. Configuration files in particular (indicated with a “c”) are expected to change over time.
However, any unusual modifications should be flagged and investigated through the system audit log. If these modifications are unneeded or suspicious in any way, the package should be reinstalled using:
# sudo yum reinstall <packagename>
Just as system files and commands have a cryptographic hash, software sources have their own type of a digital signature in the form of repository metadata. It’s important to verify the authenticity of any software before installing it to ensure that it comes from a trusted source, and that no changes have been made from the vendor version. This is equally important for any subsequent upgrades, patches, service packs, device drivers, or operating system components. Making sure the signature matches vendor’s signature ensures no tampering has occurred.
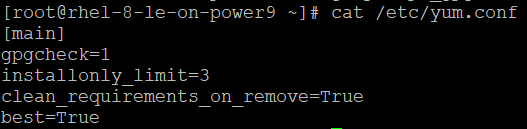
Make sure that that yum verifies the package metadata prior to install with the following command:
# grep repo_gpgcheck /etc/yum.conf
repo_gpgcheck=1