Chapter 1 | Verify Defaults and Functionality
System files and directories have default ownership and permissions that are recommended from the creator of the package. File permissions, ownership, and group membership of system files and commands are most secure if they match those recommended values. However, over time, these permissions and ownership may have been altered from the defaults for various reasons, either accidental or intentional, out of malice or ignorance. Since the default permissions typically follow the practice of least privilege, it’s best to return to these defaults as they provide the right amount of access only to those that need it. It’s also worth checking permissions on a regular basis, to ensure the wrong access levels or incorrect owners aren’t in place for too long.
First, check the file permissions and ownership of system files and commands:
# rpm -Va | grep '^.M’
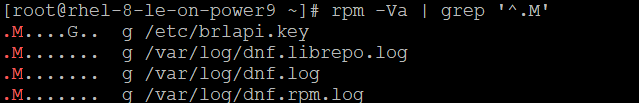
This command performs an audit of the files and directories that come from packages, reporting differences if any exist. The output flags differences, as follows:
S—File size differs
M—Mode differs (includes permissions and file type)
5—MD5 sum differs
D—Device major/minor number mismatch
L—ReadLink(2) path mismatch
U—User ownership differs
G—Group ownership differs
T—mTime differs
If the audit finds any issues, you’ll want to reset them. First, you’ll need to find out which package owns the file:
# rpm -qf <filename>
Now that you have the package name, you can begin to fix any of the issues found. For example, if the mode (M) differs, you can reset the permissions of all the files that come from that package back to the default:
#rpm --setperms <packagename>
Or, if the user (U) or group (G) ownership of a file is incorrect, you can also reset it, using:
#rpm --setugids <packagename>
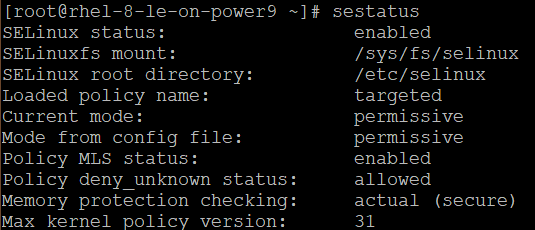
Once you have ensured ownership and permissions are the default settings, you should also verify the functionality of SELinux, which is a module that enforces mandatory access control, which limits users to the security policies set by the administrator. Make sure yours is both active and enforcing the targeted policy by checking its status.
# sestatus