Penetration Testing
What Is Penetration Testing?
A penetration test, or pen test, is an attempt to evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, services and application flaws, improper configurations or risky end-user behavior. Such assessments are also useful in validating the efficacy of defensive mechanisms, as well as end-user adherence to security policies.
It might be helpful to think of penetration testing as trying to see if someone can break into your house by doing it yourself. Penetration testers, also known as ethical hackers, evaluate the security of IT infrastructures using a controlled environment to safely attack, identify, and exploit vulnerabilities. Instead of checking the windows and doors, they test servers, networks, web applications, mobile devices, and other potential entry points to find weaknesses.
Keep reading:
Why is Pen Testing Important?
- Identify and Prioritize Security Risks: Pen testing evaluates an organization’s ability to protect its networks, applications, endpoints and users from external or internal attempts to circumvent its security controls and gain unauthorized or privileged access to protected assets.
- Intelligently Manage Vulnerabilities: Pen tests provide detailed information on actual, exploitable security threats. By performing a penetration test, you can proactively identify which vulnerabilities are most critical, which are less significant, and which are false positives. This allows your organization to more intelligently prioritize remediation, apply needed security patches, and allocate security resources more effectively to ensure that they are available when and where they are needed most.
- Leverage a Proactive Security Approach: These days, there's no one solution to prevent a breach. Organizations must now have a portfolio of defensive security mechanisms and tools, including cryptography, antivirus, SIEM solutions, and IAM programs, to name a few. However, even with these vital security tools, it's difficult to find and eliminate every vulnerability in an IT environment. Pen testing takes a proactive approach, uncovering weaknesses so that organizations know what remediation is needed, and if additional layers should be implemented.
- Verify Existing Security Programs Are Working and Discover Your Security Strengths: Without the proper visibility into your environment as a whole, changing your security posture may result in you eliminating something that was not actually problematic. Pen tests don't only tell you what isn't working. They also serve as quality assurance checks, so you'll also find out what policies are most effective, and what tools are providing the highest ROI. With these insights an organization can also intelligently allocate security resources, ensuring that they are available when and where they are needed most.
- Increase Confidence in Your Security Strategy: How can you be confident in your security posture if you do not effectively test it? By regularly putting your security infrastructure and your security team through their paces, you won't have to wonder hypothetically what an attack will look like and how you'll respond. You'll have safely experienced one, and will know how to prepare to ensure your organization is never caught off guard.
- Meet Regulatory Requirements: Penetration testing helps organizations address the general auditing and compliance aspects of regulations and industry best practices. By exploiting an organization’s infrastructure, pen testing can demonstrate exactly how an attacker could gain access to sensitive data. As attack strategies grow and evolve, periodic mandated testing makes certain that organizations can stay one step ahead by uncovering and fixing security weaknesses before they can be exploited. Additionally, for auditors, these tests can also verify that other mandated security measures are in place or working properly. The detailed reports that pen tests generate can help organizations illustrate ongoing due diligence to maintaining required security controls.
Keep reading:
- Assess the Effectiveness of Your Security Controls with Penetration Testing
- How Manture is Your Vulnerability Management Program?
Who Performs Penetration Tests?
One of the biggest hurdles in creating a successful cybersecurity program is finding people with the right qualifications and experience. The cybersecurity skills gap is well-documented issue with a qualified supply of security professionals not keeping up with demand. This is particularly true with pen testing. Unfortunately, there is no shortage of threat actors and cybercrime groups. Consequently, organizations can’t delay deploying critical pen testing initiatives.
But even with the skills gap, businesses can build a strong pen testing program by intelligently using the resources that are readily available because not every test requires an expert. Penetration testing tools that have automated features can be used by security team members who may not have an extensive pen testing background. These tools can be used for tests that are easy to run, but essential to perform regularly, like validating vulnerability scans, network information gathering, privilege escalation, or phishing simulations.
Of course, expert pen testers are still a critical part of pen testing. For complex tests that require delving deep into different systems and applications, or running exercises with multiple attack chains, you’ll want a person or team with more experience. In order to test a realistic attack scenario, you’ll want a red team that uses sophisticated strategies and solutions similar to threat actor techniques.
Keep reading:
- How To Manage the Pen Testing Skills Shortage
- 3 Reasons Every Organization Should Leverage Third-Party Pen Testers
How Does Pen Testing Work?
Penetration testing is typically performed using manual or automated technologies to systematically compromise servers, endpoints, web applications, wireless networks, network devices, mobile devices and other potential points of exposure. Once vulnerabilities have been successfully exploited on a particular system, testers may attempt to use the compromised system to launch subsequent exploits at other internal resources, specifically by trying to incrementally achieve higher levels of security clearance and deeper access to electronic assets and information via privilege escalation.
Information about any security vulnerabilities successfully exploited through penetration testing is typically aggregated and presented to IT and network system managers to help those professionals make strategic conclusions and prioritize related remediation efforts. The fundamental purpose of penetration testing is to measure the feasibility of systems or end-user compromise and evaluate any related consequences these incidents may have on the involved resources or operations.
Through penetration testing, you can proactively identify the most exploitable security weaknesses before someone else does. However, there’s a lot more to it than the actual act of infiltration. Pen testing is a thorough, well thought out project that consists of several phases:
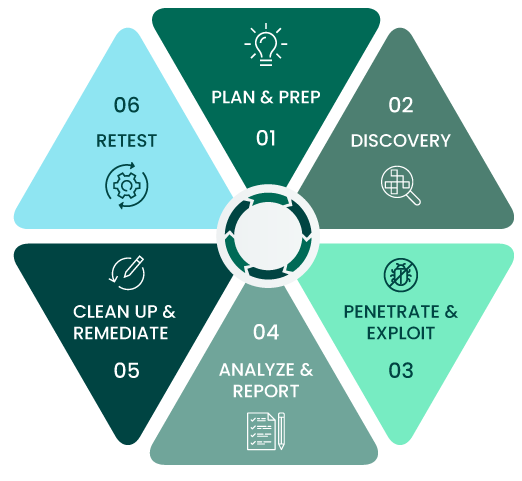
1. Planning & Preparation - Figure out goals and scope accordingly.
3. Penetration & Exploitation - Test security weaknesses, gain access, and elevate privileges.
5. Clean Up & Remediation - Leave no trace of testing activities and fix discovered weaknesses.
2. Discovery - Perform different types of reconnaissance on their target.
4. Analysis & Reporting - Report what is putting an organization most at risk.
6. Retesting - Ensure fixes were implemented and discover new weaknesses.
Keep reading:
Want to learn more about pen testing?
Check out our pen testing toolkit which is designed to guide you through all the steps of managing an effective penetration testing program.
How Often Should You Pen Test?
Penetration testing should be performed on a regular basis to ensure more consistent IT and network security management. A pen-tester will reveal how newly discovered threats or emerging vulnerabilities may potentially be assailed by attackers. In addition to regularly scheduled analysis and assessments required by regulatory mandates, tests should also be run whenever:
Network infrastructure or applications are added
Security patches are applied
Upgrades to infrastructure or applications are done
End user policies are modified
New office locations are established
What Should You Do After a Pen Test?
Going through the results of pen tests provides a great opportunity to discuss plans going forward and revisit your security posture overall. Seeing pen tests as a hoop to jump through and simply checking it off a list as “done” won’t improve your security stance. It’s important to plan time for a post-mortem to disseminate, discuss, and fully understand the findings. Additionally, relaying these results with actionable insights to decision makers within the organization will better emphasize the risk that these vulnerabilities pose, and the positive impact that remediation will have on the business. With review, evaluation, and leadership buy-in, pen test results can transform into action items for immediate improvements and takeaways that will help shape larger security strategies.
Keep reading:
What Is the Difference Between Vulnerability Scans and Pen Tests?
Vulnerability scanners are automated tools that examine an environment, and upon completion, create a report of the vulnerabilities uncovered. These scanners often list these vulnerabilities using CVE identifiers that provide information on known weaknesses. Scanners can uncover thousands of vulnerabilities, so there may be enough severe vulnerabilities that further prioritization is needed. Additionally, these scores do not account for the circumstances of each individual IT environment. This is where penetration tests come in.
While vulnerability scans provide a valuable picture of what potential security weaknesses are present, penetration tests can add additional context by seeing if the vulnerabilities could be leveraged to gain access within your environment. Pen tests can also help prioritize remediation plans based on what poses the most risk.
Keep reading:
- Top 14 Vulnerability Scanners for Cybersecurity Professionals
- Better Together: How Pen Testing Helps Take Vulnerability Assessments to the Next Level
What Are the Different Types of Pen Testing?
While it's tempting to just request that at tester "test everything," this would most likely lead to pen testers only scratching the surface of a number of vulnerabilities, sacrificing gathering valuable intelligence gained by going more in-depth in fewer areas, with clear objectives in mind. In order to make sure pen tests can achieve these objectives and pinpoint weaknesses, there are various different types of pen tests that focus on different areas of an IT infrastructure, including:
- Web Application Tests: Web application penetration tests examine the overall security and potential risks of web applications, including coding errors, broken authentication or authorization, and injection vulnerabilities.
- Network Security Tests: Network penetration testing aims to prevent malicious acts by finding weaknesses before the attackers do. Pen testers focus on network security testing by exploiting and uncovering vulnerabilities on different types of networks, associated devices like routers and switches, and network hosts. They aim to exploit flaws in these areas, like weak passwords or misconfigured assets, in order to gain access to critical systems or data.
- Cloud Security Tests: Security teams to work with cloud providers and third-party vendors to design and carry out cloud security testing for cloud-based systems and applications. Cloud pen testing validates the security of a cloud deployment, identifies overall risk and likelihood for each vulnerability, and recommends how to improve your cloud environment.
- IoT Security Tests: Pen testers take the nuances of different IoT devices into account by analyzing each component and the interaction between them. By using layered methodology, where each layer is analyzed, pen testers can spot weaknesses that may otherwise go unnoticed.
- Social Engineering: Social engineering is a breach tactic, which involves using deception in order to gain access or information that will be used for malicious purposes. The most common example of this is seen in phishing scams. Pen testers use phishing tools and emails tailored to an organization to test defense mechanisms, detection and reaction capabilities, finding susceptible employees and security measures that need improvement.
White Box, Black Box, and Gray Box Penetration Testing
When it comes to white, black, or gray box testing, defining each style can fall into three categories. Each category depends on the initial information provided prior to the pen test itself.
- White Box Penetration Testing: White box pen testing shares the full network and system information with the pen tester. All credentials, mapping, system and network information are given to the pen tester to enable a pen tester to focus on exploiting a target without needing an outside attack methodology to gain initial entry, creating an assumed breach scenario. White box pen testing targets specific systems with multiple attack vectors with as little difficulty and interruption as possible.
- Black Box Penetration Testing: Black box pen testing is the opposite of white box, in that zero information is shared with the pen tester. This requires a tester to perform reconnaissance. determine attack paths. This is considered an authentic external test, in which a pen tester would use the same methods an attacker would use to compromise security measures to gain initial access to a company’s systems and potentially pivoting throughout the environment. This attack test requires the most time and resources since there is no prior knowledge of a company’s infrastructure.
- Gray Box Penetration Testing: Gray box pen testing is a mix of white and black box attack methods. Limited information is provided to testers, typically login credentials, but other privileged information is withheld. Gray box testing is useful when an organization would like to see what an attack would look like should a cybercriminal be able to acquire access information, however, they don’t have a roadmap of pertinent network and system information. Gray box testing allows a company to assume credentials have already been compromised, and doing so, what potential damage can be caused from this style of breach.
How Does Pen Testing Help With Compliance?
Cybersecurity teams typically have to ensure that they are maintaining compliance with regulations like:
- HIPAA
- PCI DSS
- SOX
- NERC
- HEOA
- GDPR
- CMMC
By exploiting an organization’s infrastructure, pen testing can demonstrate exactly how an attacker could gain access to sensitive data. As attack strategies grow and evolve, periodic mandated testing makes certain that organizations can stay one step ahead by uncovering and fixing security weaknesses before they can be exploited. Additionally, for auditors, these tests can also verify that other mandated security measures are in place or working properly.
For instance, many of these regulations either imply or specifically require pen testing as a way to evaluate an organization’s security posture and adherence. Requirement 11.3 of the Payment Card Industry Data Security Standard (PCI DSS), for example, states that a comprehensive pen testing program must be implemented.
Keep reading:
What Is Teaming?
The number of attacks are increasing and the amount of research and experience that’s required to get ahead of these attacks is expanding the gap between time of attack and time of discovery. That’s where teaming comes in. Teaming exercises simulate real-life attack scenarios--with one team attacking, and another defending.
Red Teams
A red team is on the offensive side. A red team is formed with the intention of identifying and assessing vulnerabilities, testing assumptions, viewing alternate options for attack, and revealing the limitations and security risks for that organization.
Blue Teams
The blue team is tasked with defending the organization. Blue teams are in charge of building up an organization’s protective measures, and taking action when needed.
Purple Teams
Recently, the concept of a purple team has become more popular in teaming exercises. This is the mindset of seeing and treating red and blue teams as symbiotic. It’s not red teams vs. blue teams, but rather one large team focusing on the one overarching goal: improving security. The key to becoming a purple team comes down to communication between individuals and their teams.
Learn more about teaming:
What Are Pen Testing Tools?
Attackers use tools in order to make their breach attempts more successful. The same is true for pen testers. Penetration testing software is intended for human augmentation, not replacement—they allow pen testers to focus on thinking outside the box by taking over tasks that take time, but not brain power. When it comes to pen testing, it’s never a choice between penetration testing tools vs. penetration testers. Instead, it’s a choice of what penetration tools will help a penetration tester most.
Penetration testing is typically completed using a portfolio of tools that provide a variety of functionalities. Some are open source, while others are commercial. Some of these tools are the same as those used by threat actors, allowing for the exact replication of an attack. Others highlight the needs of an ethical hacker, allowing for a stronger emphasis on features that prioritize the end goal of validating security weaknesses without affecting production environments, and prioritizing remediation.
Security teams are also turning to penetration testing tools to advance their in-house programs through strategic automation. Automation can elevate the skills of inexperienced testers with wizards that safely guide them through critical standard tests; experienced testers can maximize their time by automating the routines.
So what should you look for when it comes to an automated pen testing solution? Penetration testing tools should be simple, efficient, reliable, and centralized.
Keep reading:
- The Human Element of Pen Testing and the Role Tools Can Play
- How Commercial Pen Testing Tools Can Make Your In-House Testing Program More Effective and Efficient
- Three Things You Need in a Penetration Testing Tool
How to Choose Between a Penetration Testing Tool or Service
Pen testing software and services are one of the top ways to evaluate an organization’s ability to secure networks, applications, endpoints, and users from exploitation of security weaknesses. However, depending on your circumstances, you may have to choose between software and services. Other times, you’ll need both. So how do you determine which approach you need?
First, you’ll need to evaluate your company’s size and structure. If you have on-staff security analysts, perhaps automated tools are the best option. External pen testing services can give an outside perspective of your cybersecurity needs. The combination of both is the best way to ensure some of the strongest coverage.
The guide When to Use Penetration Testing Software, Services, or Both gives detailed advice to help determine what level of pen testing your company needs, by examining pen testing scope, organization size and structure, tools and resources available, analyst skills and experience, and implementation timeline.
How Are Exploits Used in Pen Testing?
A common tactic of attackers trying to breach an environment is to use an exploit against a known vulnerability in an application or device present in a targeted infrastructure. Exploiting a vulnerability can provide an attacker with privileges or capabilities they would not normally be granted. In order to provide insight into what threat actors might be able to do, pen testers also use exploits.
Usually, attackers have to write exploits as they find vulnerabilities. Others are readily available on the internet, usually posted anonymously by other attackers.
On the ethical hacking side, exploit development can be an advanced penetration testing skill that takes time to master. Additionally, when on a job, pen testers often don’t have the resources to create a new exploit. Many resort to searching for and using pre-written exploits they find online—oftentimes the same ones attackers use.
Because exploit writing takes time and expertise, both attackers and pen testers alike are always looking for exploits or exploit libraries that can save them the effort. Access to enterprise exploit libraries are often a benefit that comes with owning an enterprise pen testing tool.
Keep reading:
Penetration Testing Solutions from Core Security
Penetration Testing Services
Identify the security gaps that are putting your organization at risk.