Common Security Concerns and How to Reduce Your Risk
What common security risks/entry points are you most concerned about?
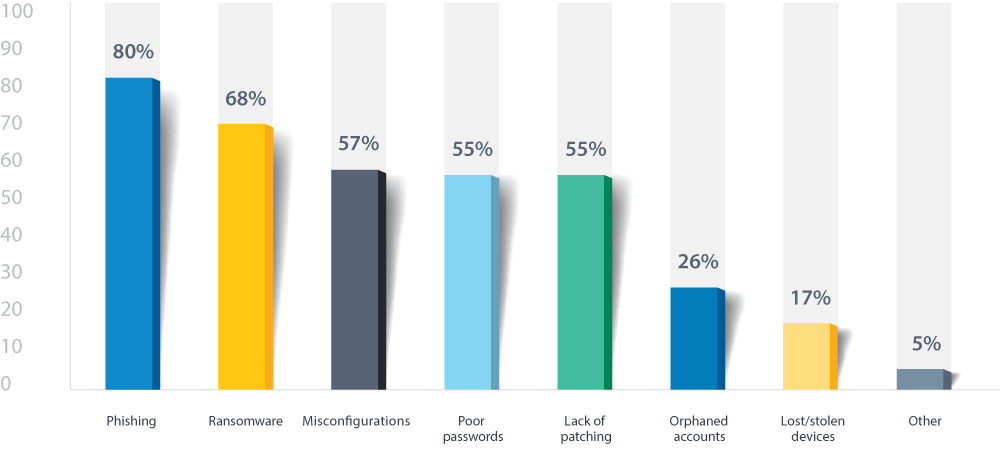
In our 2023 Pen Testing Survey we asked what common security risks concerned respondents most. While phishing (70%) and ransomware (72%) were the top concerns, other options had a high enough percentage to warrant further discussion. These included:
• Misconfiguration
• Poor passwords
• Lack of patching
• Orphaned accounts
• Lost/Stolen devices
Read on to learn why these issues continue to stay top of mind for security professionals and what can be done to safeguard your organization against them.
Common Security Concerns
1. Phishing
At 80%, phishing surpassed misconfigurations as the top concern—and for good reason. Since phish regularly evade spam filters, it can be difficult to prevent users from being regularly exposed to this problem. Phishing is also becoming increasingly challenging to spot, with sophisticated tactics designed to entice users to open them without question. For example, spear phish look incredibly realistic and are tailored for specific people or groups.
Phishing simulations imitate malicious phishing campaigns, allowing organizations to monitor whether any are opened, clicked, or have credentials entered. These simulations can assist in uncovering which employees are vulnerable to phishing, and what type of phish they’re likely to open. From there, regular reeducation sessions for those who fail phishing simulations can help create more discerning users.
2. Ransomware
Ransomware has skyrocketed as a concern as high-profile shutdowns and ransom demands dominate news cycles. At its most basic level, ransomware is a type of malware that attackers use to hold data hostage unless a ransom is paid. Ransomware now accounts for 10% of all breaches, doubling its prevalence in one year, and more than one-third of global organizations said they were victimized by some sort of ransomware in 2021.
Ransomware has grown in numbers and sophistication within the last few years. Some criminals even offer ransomware as a service (RaaS), renting malware platforms for other criminals to exploit. There’s no guarantee that attackers will release the data once a ransom is paid, returning to the company (or even its customers) for additional extortion attempts by threatening to sell or publicize sensitive information.
3. Misconfigurations
Misconfigurations, and particularly cloud misconfigurations, have been to blame for a number of large breaches over the years. Even when security policies are properly configured at the start, they can often be altered at any time by any employee. Luckily, there are clear steps to successfully keep misconfiguration mistakes to a minimum.
Limit access. Users that have full access to their networks can end up in an application they aren’t familiar with and accidentally change something. A strong Identity Access Management (IAM) program, whether through Identity Governance or Privileged Access Management solutions, can enforce the principle of least privilege by only giving employees the privileges they need to complete their job functions.
Monitor and manage security configuration. Since misconfigurations are so frequently accidental, they can go undetected for months, and all too often a breach is what notifies security teams of a vulnerability. Configurations of servers and networks should be routinely checked to verify that they adhere to your organization’s security policy. While this can be a challenge, especially with cloud servers regularly spinning up new instances, there are tools that can automate this administration and ensure efficiency. Additionally, configuration policies should be continuously monitored to ensure unauthorized changes don’t go unnoticed. It can be difficult to do this manually, so security monitoring tools like SIEM solutions can help keep track of any modifications to your organization’s policy.
4. Poor Passwords
Passwords are limited, but are still regularly used within companies. Weak passwords and ineffective password management are a major threat to the security of an organization’s sensitive data. It is essential to have a strong password management solution and maintain password policies that enforce complexity and non-reuse rules. But this must be done in a way that leverages secure and flexible authentication methods. A variety of password reset authentication options, including mobile reset applications, telephone-based keypad resets, or voice biometrics increase user adoption rates, while maintaining a secure reset channel.
5. Lack of Patching
Lack of patch management appears as a top security concern for the first time, underscoring the criticality of fixing known vulnerabilities as soon as practical. Even the smallest companies have dozens — if not hundreds — of software programs and connections that could require patches. Threat actors are quick to exploit new patches by reverse engineering them, discovering the vulnerability the patch is designed to fix.
The key to patch management success is to create a comprehensive inventory of assets, monitor patches and apply them immediately, and use automated penetration testing tools like Core Impact can run remediation validation tests to ensure that a vulnerability has been patched and can no longer be exploited.
6. Orphaned Accounts
Orphaned accounts are accounts that are still active in the network, but are no longer being used, typically because the user no longer works at the organization. While all organizations can have orphaned accounts, certain businesses are more susceptible—those with high turnover, a contingent workforce, seasonal employees, or those that have been through an institutional change, like a merger or acquisition. Since orphaned accounts are no longer associated with a valid user, they are an ideal way for attackers to gain access into an organization because no one is actively looking into them. Orphaned accounts are similar to misconfigurations in that they are typically accidental and consequently often linger. Luckily, they can also be managed with a comprehensive Identity Governance & Administration (IGA) program.
Orphaned accounts are a common identity management problem, so an IGA program would include policies on provisioning and deprovisioning accounts with the user lifecycle in mind. This would take into account the type of user when it is first created—full-time employee, temporary employee, vendor, or contractor—as well as the necessary measures needed upon departure, whether it be voluntary or termination. Because of the complexities of these policies, there are solutions designed to automate this process that will mitigate the ongoing risk of orphaned accounts.
7. Lost or Stolen Devices
While it’s incredibly convenient to have employees able to work from anywhere using laptops, tablets, or other issued devices, it has made the potential for loss or theft increase exponentially. While it’s impossible to prevent this from happening altogether, it’s important to have a policy in place that encourages employees to report these events as soon as possible. Security monitoring solutions may also be able to detect a stolen device before it’s been reported. These solutions can be set up to trigger alerts for abnormal behavior like repeated logon attempts, sessions from unusual locations or during odd hours, as well as any other suspicious activity.
Additionally, some measures can be taken to ensure that there is no damage aside from the cost and inconvenience of a lost device. Where possible, devices should be password or biometrically protected, and have an option of wiping them remotely.
Prioritizing Security Weaknesses With Penetration Testing
All of the above concerns are valid, and require some sort of action in order to mitigate the danger they pose. But solutions to these issues take time, money, and resources, so organizations must be strategic in how they choose to address them. Penetration testing, which involves using the same techniques as attackers, exploiting your own network to uncover security weaknesses, provides valuable, actionable intelligence that will help you make such decisions.
Pen testing not only discovers which entry points have been left unprotected in your network, it helps you intelligently manage these vulnerabilities by determining how much risk they each pose. Additionally, retesting helps determine if changes made are improving your defenses. By regularly evaluating your infrastructure in this way, you can begin to build the most successful layered security posture for your organization.
Want to learn more pen testing insights?
Read the full 2023 Pen Testing Survey Report to get a comprehensive picture of the effectiveness of ethical hacking strategies, and the resources required to deploy a successful pen testing program.