Oftentimes after using Network Information Gathering, we are still left with a number of devices that may reflect an "Unknown" OS. With the saturation of these devices in the market today, there is a good chance there may be some located on your network. By identifying these devices we can also potentially expand our attack surface and gain other useful information.
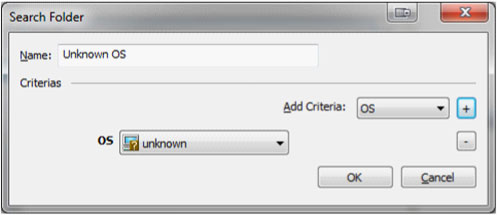
So, where do we start? We may as well create a new search folder so that only the machines that reflect "unknown" under the OS column can be viewed.
To do this, right-click on "Search Folders", select "New" -> "Search Folders..." and at this point a window should pop up where the criteria for the search folder can be selected. A good name for this folder would obviously be "Unknown OS".
In the dropdown next to "Add Criteria" select OS and click the "+", then make sure "Unknown" is selected and click "OK". At this point you should now expand "Search Folders" and select the one that we just created. Now in the host view you should only see machines that have an unknown OS.

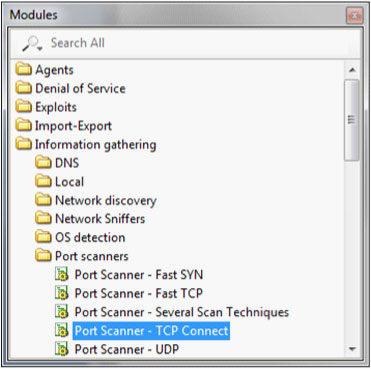
Next go into the module view and select Information gathering, then Port scanners, then choose "Port Scanner -TCP Connect" and drag it over the network that contains all of the unknown boxes.
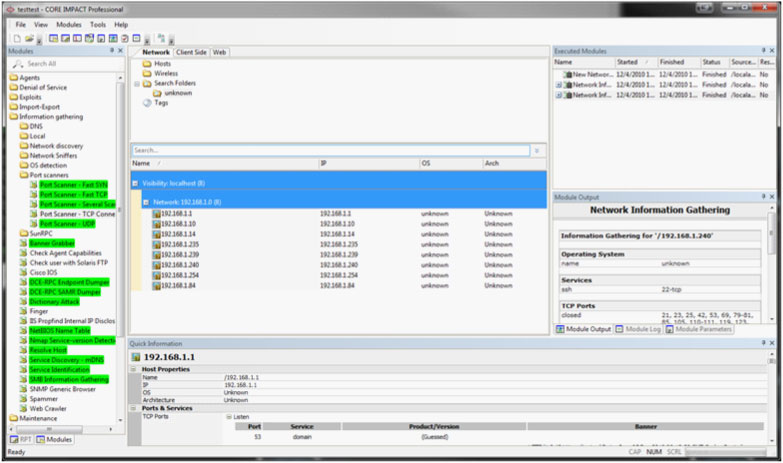
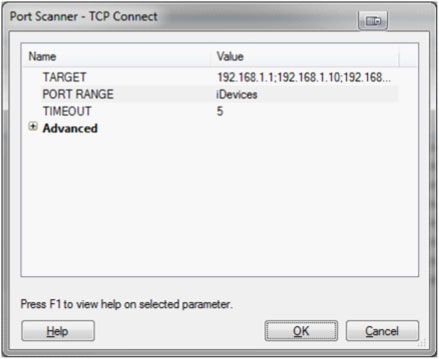
That should automatically select all unknown boxes in that particular network. In the row labeled "PORT RANGE" click in the value section and then click the ellipses (...). From here it may be useful to create a new group. Go ahead and click the "New" button. For the group name I chose to call mine "iDevices" but you can choose whatever you like. Next click the "New" icon next to port ranges and add 62078 and click "OK". Port 62078 is a sync port that just happens to be open on these particular devices and is what we will be using to fingerprint them. At this point you can put a check next to our new group and make sure the others are unchecked and then click "OK".
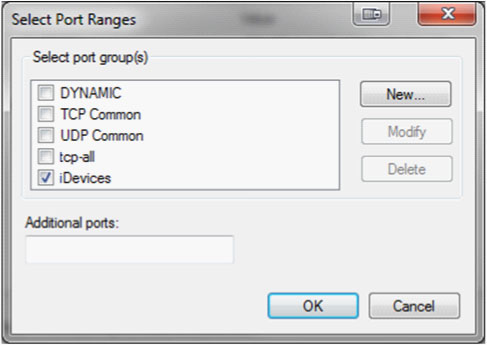
Now make sure that all the targets you wish to scan are selected and click "OK" here as well.
Once this has finished, it's time to go back up and create a new search folder just as we did earlier. This time the criteria will be a bit different. Once again we will select "unknown" OS, but we will also add TCP port 62078 with a status of listen. Once this is done, click "OK".
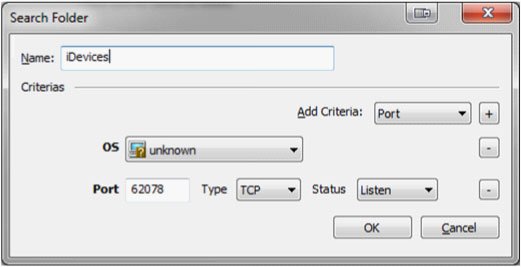
Click the folder we just created, and now with any luck you will see some devices in this list. The most likely scenario is that these are some type of iDevice. At this point by clicking on our search folder we can tell at a quick glance what these devices are, even though they still reflect an unknown status in the OS column.
So how do we take advantage of this? If there is any chance that your users may be the type to jailbreak their devices, look at the list of iDevices and see if any of them have port 22 open. If a user has not specifically changed their root password and they happen to have SSH open on their device, you can login as root with the default password of “alpine.” You now have access to all the data on their phone. I would suggest poking around the /private/var/mobile/Library directory and seeing what fun things you can find...There is quite possibly some information on these devices that could help you gain a little ground in your pentest.