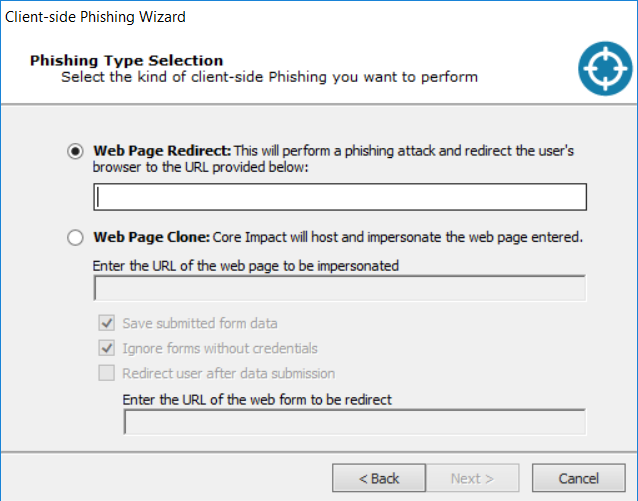
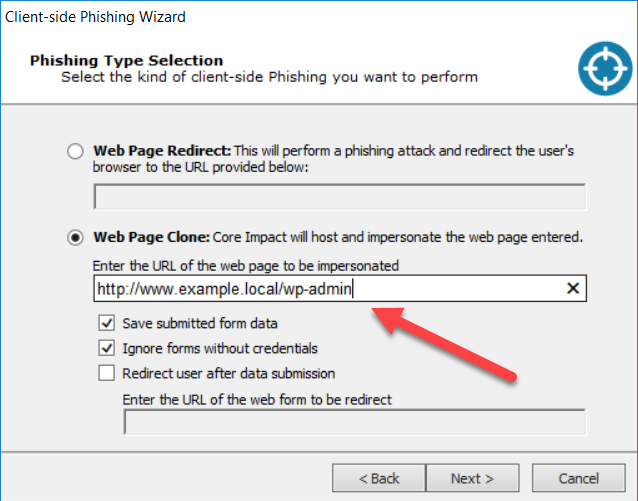
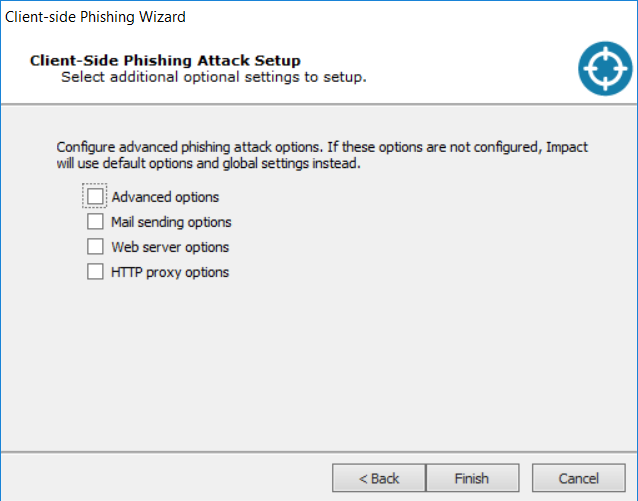
Core Impact 18.1 release brought a ton of streamlined enhancements and new capabilities to the client-side vector in general, and phishing in particular. To be clear on terms, I consider phishing to be inducing a target to follow a link presented in an email for the purposes of capturing credentials for some system or another. Using an email to get a user to overtly run a compromised attachment or covertly execute an exploit payload falls under the broader client-side umbrella.
I want to take a few minutes to walk through some of the changes and new features in the product - if you’ll indulge me.
First off, I want to point out that we’ve gone and separated the Phishing Attack Phase RPT wizard from the Attack and Penetration RPT for Client Side.