Core Impact in 20 Minutes | Attacking Web Applications
This video will cover how to attack web applications using Core Impact.
This tutorial focuses on attacking web applications with Core Impact, which is just one of the vectors included in the solution. You’ll want to start by creating a new workspace within Core Impact.
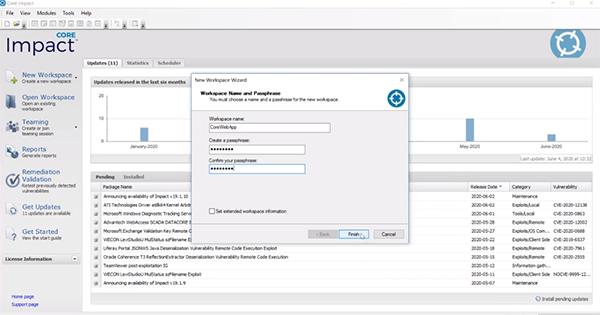
Information Gathering
Core Impact works with several other tools including vulnerability scanners. For example, the solution can ingest scanner data for a web application to user some the details you’ve gathered there and enhance them in the post-exploitation phase. For this tutorial we’ll start by using Core Impact to crawl a site to do some of the information gathering ourselves.
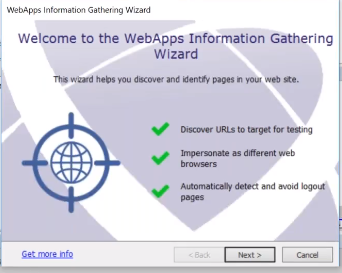
The pages we’ll attack are MetaSploitable 2 with Mutillidae that are good to practice against. The first step is to crawl the site using the RPT in Core Impact. You can enter the URL of the website you’d like to crawl or select “interactive web crawling” which gives you a little more flexibility. Keep the remainder of the settings of the information gathering wizard set to default.
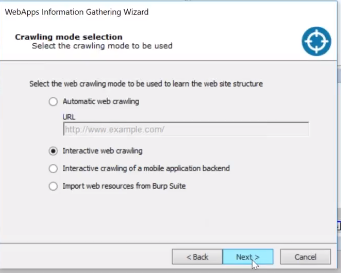
Proxy Settings
Now the scenario has been created and it will house all the webpages. When you open up your scenario it will ask you to configure your proxy settings. You’ll need to change it to local host and turn on your proxy server to put it in capture mode.
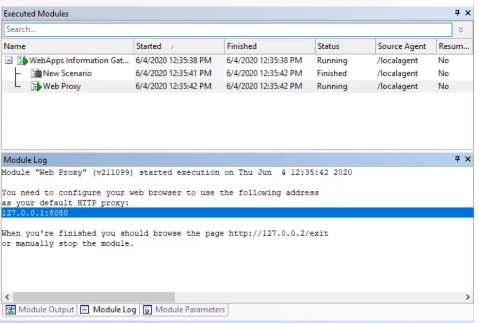
SQL Injection
The first thing we’ll do is SQL injection on the on the Mutillidae site and try to login. After doing so, you can now go back to Core Impact and stop the system from crawling the web application.
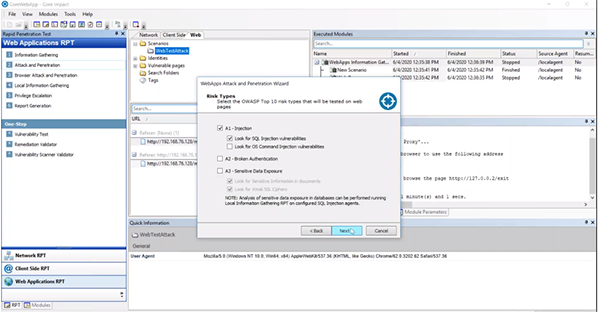
SQL Injection Attack and Penetration
In this first example we’ll focus on SQL injection. Grab the “Attack and Penetration” RPT and pull it over to the scenario. Deselect everything but “A1 – Injection.” We do want to test the cookie information so make sure that is selected. When it comes to SQL injection, Core Impact can test for unions, blinds, and different input in fields for different layers of fuzzing.
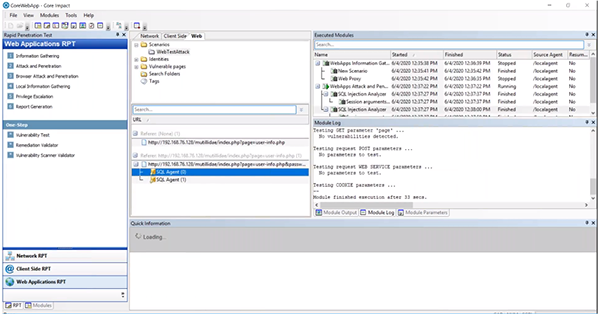
Once finished, Core Impact will automatically start attacking the pages and we can actively see what is happening. We were easily able to identify a SQL injection vulnerability and because we now have a SQL agent, it will give us post-exploitation capabilities.
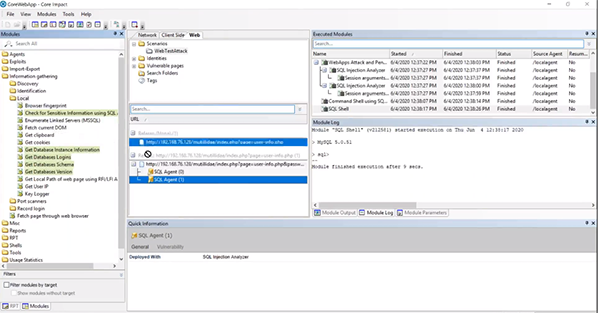
SQL Agent Post-Exploitation
From the SQL agent, we can launch a Command Shell or a SQL Shell. Within Core Impact we can do some post-exploitation and local information gathering to show us sensitive information we can utilize. Under the “Information Gather” and “Local” folder, drag “Check for Sensitive Information using SQL” over to your agent. This allows us to look for credit card numbers and social security numbers. You can also pull other the “Databases Schema” to the agent to identify tables that may be vulnerable and need to be sanitized.
We can now use the data from the schema to run a SQL Shell and see if we can’t identify the actual credit card numbers. Right click on the agent to run a “SQL Shell” and enter a simple prompt to view all the vulnerable data. At this point, we have enough proof to go back to the organization and show what information is vulnerable.
Cross Site Scripting (XSS)
For our next example, we can do another crawl using the same scenario from before with an interactive web crawl. On the Mutillidae site, you’ll select Cross Site Scripting (XSS) and DNS lookup. In this example we attempted facebook.com. After doing so, you can now go back to Core Impact and stop the system from crawling the web application.
Cross Site Scripting Module
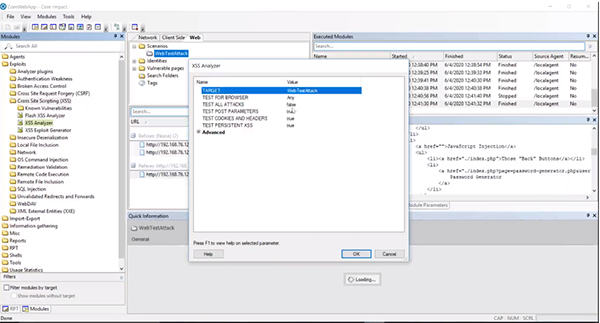
We now have the URL captured in Core Impact and we can go the “Modules” section. Within the “Exploits” folder there is a “Cross Site Scripting (XSS)” folder. Select the “XSS Analyzer" and drag it over to the scenario. This may take a little time to run.
XSS Post-Exploitation
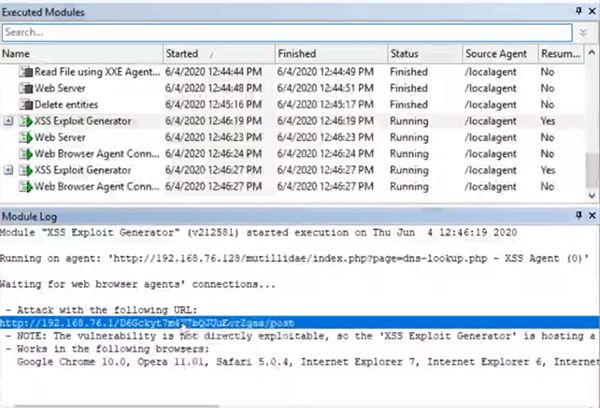
Now that we have a XSS agent, we can use the “XSS Exploit Generator” module on the agents you have. You can keep the settings set to the default. Within the Module Log, you’ll see a URL you can use to attack. Make sure your proxy server settings are turned off and paste the URL into a browser.
Browser Agent
What this does is generates a browser agent. So if you send a user this link and they click on it, you should be able to interact with the browser within Core Impact. For example, you could put a key logger on the browser agent and track what the user is doing.
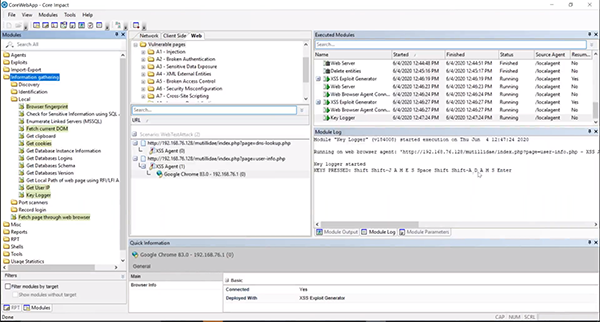
You can now show your organization what web applications are vulnerable and exploitable in addition to the risks that it brings.