Core Access Insight
Intelligent identity analytics to address immediate threats, improve ongoing provisioning, and enhance governance across your enterprise
Access Insight offers a continuous, comprehensive view and analysis of the relationship between identities, access rights, policies, and resources that occur across your entire environment. Our easy-to-use, easy-to-understand solution applies analytics to the big identity and access data in your organization, empowering you to identify identity-related access risks, and drive provisioning and governance controls to manage that risk within your business.
Identify, Prioritize, and Manage Access Risk
With Access Insight, your governance system does more than just manage access. It provides access intelligence to analyze the identity and access data in your organization, using advanced analytics tools. This enables you to perform data mining, statistical analysis, and data visualization—drawing on specific governance policies, rules, and risk indicators to provide intelligence and valuable information for administrators, analysts, compliance officers, and incident responders. Access Insight ensures the right people have the right levels of access and enables you to visualize what that access actually means, so you can better understand, quantify, and manage access risk in your organization.
With Access Insight, your governance system does more than just manage access. It provides access intelligence to analyze the identity and access data in your organization, using advanced analytics tools. This enables you to perform data mining, statistical analysis, and data visualization—drawing on specific governance policies, rules, and risk indicators to provide intelligence and valuable information for administrators, analysts, compliance officers, and incident responders. Access Insight ensures the right people have the right levels of access and enables you to visualize what that access actually means, so you can better understand, quantify, and manage access risk in your organization.
Leverage a True Access Analytics Engine
Your organization needs deep insights on both current and historic access risk, and it must constantly monitor identity data to understand trends that affect your business. Access Insight regularly pulls in large amounts of user entitlement data and then, using a proprietary in-memory property graph, rapidly correlates identity and access relationships to identify and prioritize risks, surfacing all deeply nested and hidden relationships that exist between user identities and their granular access within an organization. These analytics identify potential risk in a current or historical perspective across lines of business, governance, operations, and applications.
Your organization needs deep insights on both current and historic access risk, and it must constantly monitor identity data to understand trends that affect your business. Access Insight regularly pulls in large amounts of user entitlement data and then, using a proprietary in-memory property graph, rapidly correlates identity and access relationships to identify and prioritize risks, surfacing all deeply nested and hidden relationships that exist between user identities and their granular access within an organization. These analytics identify potential risk in a current or historical perspective across lines of business, governance, operations, and applications.
Resolve Immediate Threats
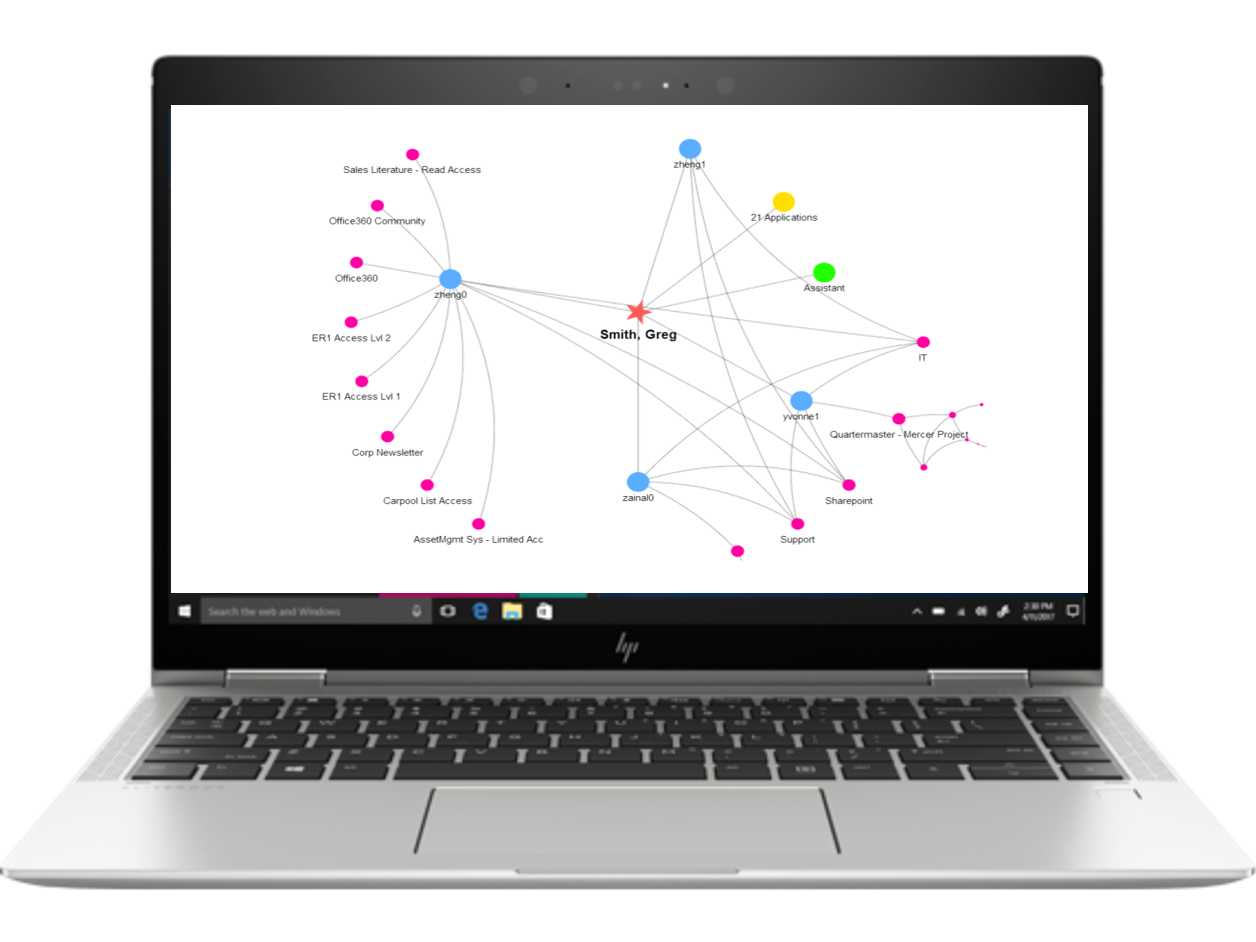
Access Insight resolves immediate threats with advanced analytics applied to the big identity and access data in your enterprise. By creating in-depth views of access through visually intuitive cues, Access Insight provides a comprehensive, real-time view of multi-dimensional relationships between identities, access rights, policies and resources across a multitude of enterprise systems and resources. Categorize and remediate access risk threats through continuous user access compliance monitoring.
Access Insight resolves immediate threats with advanced analytics applied to the big identity and access data in your enterprise. By creating in-depth views of access through visually intuitive cues, Access Insight provides a comprehensive, real-time view of multi-dimensional relationships between identities, access rights, policies and resources across a multitude of enterprise systems and resources. Categorize and remediate access risk threats through continuous user access compliance monitoring.
How the Core Access Insight Analytics Engine Works
The user-friendly dashboard from Core Access Insight offers a variety of graphical displays and interactive interfaces, so your organization’s access-related risks and risk levels can be easily viewed by business managers and authorized users.
Leveraging a proprietary in-memory property graph, our access analytics engine continuously gathers and synchronizes your organization’s identity and access information from multiple sources to compile a complete picture of identities, access rights, and resources, even deeply nested and hidden access. Automated data collection also increases operational efficiency and reduces your operational costs by eliminating labor-intensive processes to demonstrate compliance.
Continuous governance and automated policy management enables you to evaluate and act upon risks associated with user access related to corporate controls and government regulations, enabling you to proactively create and enforce your security policies.
Related Service:
Access Risk Quick Scan

Do you have a way to spot and evaluate access risks posed by internal threats across each of your business-critical systems?
Core Security provides the Access Risk Quick Scan, a consulting offering that leverages our award-winning Core Access Insight solution to diagnose access risk in your organization. The Quick Scan arms you with actionable information and insights, providing immediate visibility into risks, including:
- Orphaned accounts—accounts not associated with a valid business owner that do not have proper oversight and governance.
- Abandoned accounts—accounts that have been inactive for a specific time period that exceed policy.
- Privileged accounts—accounts with increased levels of permission that provide elevated access to critical networks, systems, applications, or transactions.
- Unnecessary entitlements—entitlements that have been utilized in the past, but are no longer being used or monitored, posing a hidden risk.
"The Core Access Risk Quick Scan was a real eye-opener. It revealed elevated privileges that we were unaware of. We uncovered contractors that had left, but still had active accounts and we were able to take quick action to eliminate this access risk."
The Right Access Risk Intelligence Solution for Every Need
Access Insight works with any Identity Governance and Administration (IGA) solution to provide a continuous and comprehensive view of your network, while improving compliance and prioritizing access risks. Access Insight works with the industry-leading portfolio of solutions from Core Security, or in conjunction with other IGA solutions, to identify potential risks to the business, so you can quickly modify access as needed. Access Insight integrates with virtually any data sources and commonly-used security management applications, and enables you to easily configure policies that align with your organization’s corporate and regulatory policies—alerting you to intentional or unintentional violations.
Key Features
